The enterprise landscape of 2026 is vastly different from the traditional perimeter-based models of the past decade. As we navigate through this year, the shift toward decentralization, cloud-native infrastructure, and an increasingly sophisticated threat landscape has made the legacy Virtual Private Network (VPN) not just obsolete but a significant liability. Today, the conversation is no longer about whether to adopt Zero Trust but how quickly and effectively an organization can complete the transition to Zero Trust Network Access (ZTNA).
- The State of Network Security in 2026
- Core Pillars of ZTNA Architecture
- Identity-Centric Security
- Microsegmentation and Lateral Movement Prevention
- Continuous Trust Evaluation
- The Economic and Operational Case for ZTNA
- Reducing the Cost of Data Breaches
- Operational Efficiency and IT Productivity
- Enhanced User Experience
- Step-by-Step Implementation Strategy for 2026
- Phase 1: Assessment and Discovery
- Phase 2: Defining the “Protect Surface”
- Phase 3: Implementing Identity and Device Posture Controls
- Phase 4: Pilot Deployment and VPN Replacement
- The 2026 Vendor Landscape: Choosing the Right Solution
- Future Trends: AI, Quantum, and the “Neocloud”
- Conclusion: Securing the Future
The State of Network Security in 2026
As of December 2025 and moving into early 2026, the cybersecurity world is witnessing a paradigm shift. The global ZTNA market is projected to grow at a compound annual growth rate (CAGR) of over 23 percent, reaching valuations in the tens of billions of dollars. This growth is fueled by a simple reality: the traditional network perimeter has dissolved. With 70 percent of remote access deployments now favoring ZTNA over legacy solutions, the era of implicit trust is officially over.
In 2026, threat actors are leveraging agentic AI and polymorphic malware to bypass traditional signature-based defenses. This means that a single compromised credential can lead to a full-scale network breach if lateral movement is not restricted. Organizations are now prioritizing “Verify Explicitly” and “Assume Breach” as their primary operational philosophies.
Shutterstock
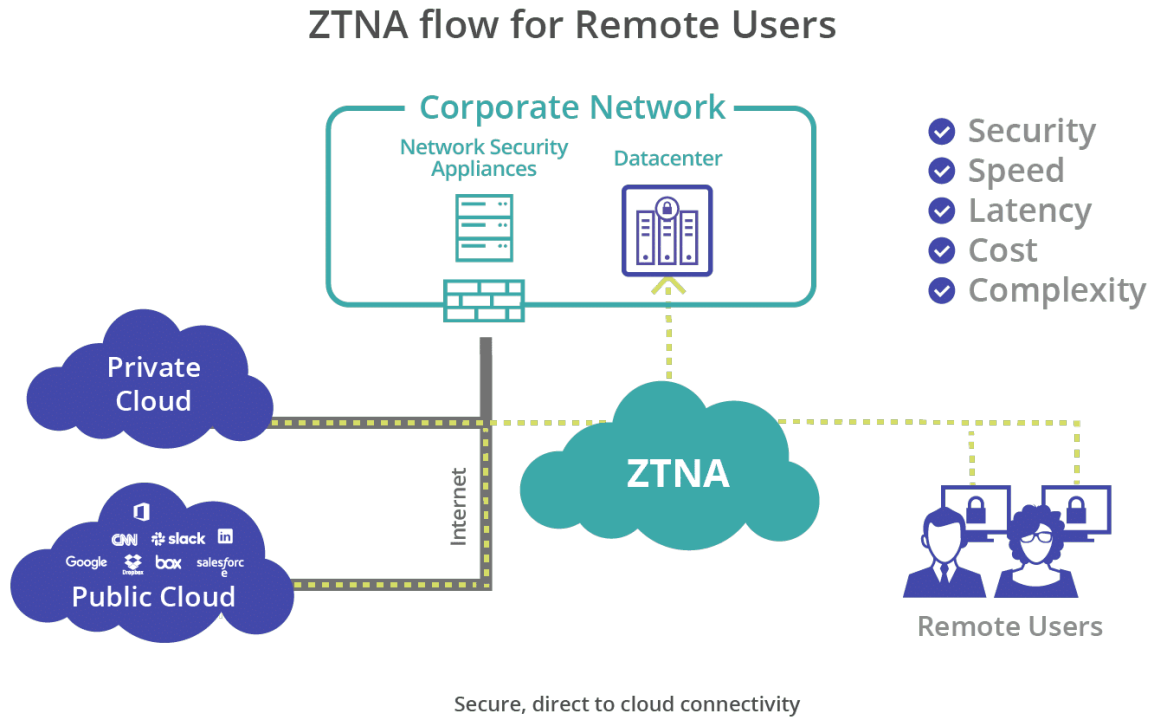
Why the Traditional VPN is a Risk Factor
For decades, the VPN was the gold standard for remote access. However, in a 2026 environment, it presents several critical flaws:
- Over-privileged Access: Once a user is “inside” the VPN, they often have broad access to the entire network segment. This is the antithesis of modern security.
- Performance Bottlenecks: Backhauling traffic to a central data center for inspection introduces latency that hinders productivity in a world of high-bandwidth SaaS applications.
- Visibility Gaps: VPNs often lack the granular logging and session-level visibility required for modern compliance and threat hunting.
- Device Posture Blindness: Many legacy VPNs do not continuously check the health of a device after the initial connection is established.
Core Pillars of ZTNA Architecture
Transitioning to ZTNA requires an understanding of the fundamental principles that govern this architecture. Unlike a VPN, which connects a user to a network, ZTNA connects a user to a specific application or resource.
Identity-Centric Security
In 2026, identity is the new perimeter. Every access request is evaluated based on who the user is, what device they are using, and the context of the request (location, time, and behavior). This involves deep integration with Identity and Access Management (IAM) providers like Okta, Microsoft Entra ID, or JumpCloud.
Microsegmentation and Lateral Movement Prevention
One of the most powerful features of ZTNA is its ability to segment the network at the application level. By creating “micro-perimeters” around individual workloads, organizations can ensure that even if an attacker gains access to one application, they cannot move laterally to another. Research shows that effective microsegmentation can reduce the impact of lateral movement by up to 80 percent.
Continuous Trust Evaluation
Trust is not a one-time event. In 2026, ZTNA solutions perform “Continuous Adaptive Risk and Trust Assessment” (CARTA). This means that if a user’s behavior suddenly changes (e.g., they begin downloading massive amounts of data or access the network from an unusual geolocation), their session can be automatically terminated or challenged with an additional MFA prompt.
The Economic and Operational Case for ZTNA
Beyond security, the transition to ZTNA in 2026 is driven by significant Return on Investment (ROI).
Reducing the Cost of Data Breaches
The average cost of a data breach has climbed toward 5 million dollars. ZTNA directly addresses the most expensive aspects of a breach: detection and containment. By limiting the “blast radius” of an attack through granular access controls, enterprises are seeing a reduction in incident response costs by nearly 40 percent.
Operational Efficiency and IT Productivity
Managing legacy firewalls and complex VPN configurations is a drain on IT resources. Cloud-delivered ZTNA simplifies the management of security policies. Instead of managing thousands of IP-based rules, admins manage human-readable, identity-based policies. This shift is allowing SecOps teams to focus on strategic threat hunting rather than manual configuration.
Enhanced User Experience
In 2026, the “user experience” is a security requirement. Slow connections lead to “shadow IT” where employees use unauthorized tools to get work done. ZTNA provides a seamless, “always-on” experience. Users no longer need to manually toggle a VPN client; they simply access their applications, and the ZTNA broker handles the security transparently in the background.
Step-by-Step Implementation Strategy for 2026
Transitioning to a Zero Trust model is a journey, not a destination. For most enterprises, a phased approach is the most effective.
Phase 1: Assessment and Discovery
Before you can protect your assets, you must know what they are. This phase involves:
- Cataloging all on-premises and cloud applications.
- Identifying “crown jewel” data that requires the highest level of protection.
- Mapping user roles and the minimum resources they need to perform their duties.
Phase 2: Defining the “Protect Surface”
Using the Kipling Method (Who, What, When, Where, Why, and How), organizations define specific policies for their most critical assets. Instead of trying to protect the entire network, focus on the “Protect Surface,” which is a much smaller, more manageable subset of the infrastructure.
Phase 3: Implementing Identity and Device Posture Controls
Strengthening identity is the first technical hurdle. This includes:
- Enforcing Phishing-Resistant MFA (such as FIDO2 keys).
- Implementing device health checks to ensure that only managed, encrypted, and patched devices can connect.
- Integrating EDR (Endpoint Detection and Response) signals into the ZTNA policy engine.
Phase 4: Pilot Deployment and VPN Replacement
Start with a non-critical application or a specific department (e.g., the IT team). Monitor the performance and user feedback. Once the pilot is successful, begin migrating remote workers off the legacy VPN and onto the ZTNA broker. By the end of 2026, the goal for most enterprises is to have 90 percent of their applications behind a ZTNA gateway.
The 2026 Vendor Landscape: Choosing the Right Solution
The market is currently crowded with excellent options, each with specific strengths. When evaluating vendors in 2026, consider the following leaders:
- Zscaler: A pioneer in cloud-native ZTNA, offering an extensive global edge network that minimizes latency.
- Fortinet: Ideal for organizations looking to integrate ZTNA with their existing firewall and SD-WAN infrastructure.
- Cloudflare: Known for its “Speed-First” approach, Cloudflare Zero Trust is highly effective for global workforces.
- CrowdStrike: Best for organizations that want to tie network access closely to endpoint security and real-time threat intelligence.
- Okta: A leader in identity-driven security, providing the foundation for modern ZTNA policies.
Future Trends: AI, Quantum, and the “Neocloud”
Looking ahead to the remainder of 2026 and into 2027, several emerging technologies will redefine ZTNA.
Agentic AI and Autonomous Defense
AI is no longer just a buzzword. Modern ZTNA platforms are utilizing “Agentic AI” to autonomously adjust security policies in real-time. If a new zero-day vulnerability is discovered, the AI can automatically restrict access to the affected application across the entire organization within seconds.
Post-Quantum Cryptography (PQC)
With the rise of quantum computing threats, the encryption used in ZTNA tunnels is being upgraded to Post-Quantum standards. Forward-thinking organizations are already asking their vendors for PQC roadmaps to ensure their data remains secure against future “harvest now, decrypt later” attacks.
Convergence with SASE
The boundaries between ZTNA, Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB) are disappearing. This convergence, known as SASE (Secure Access Service Edge), provides a single, unified platform for all security needs. In 2026, 50 percent of enterprises are expected to adopt a single-vendor SASE approach to reduce complexity.
Conclusion: Securing the Future
The transition to ZTNA in 2026 is a strategic imperative. It is the only way to protect a distributed workforce and complex cloud environments against modern threats. By focusing on identity, microsegmentation, and continuous verification, organizations can build a resilient security posture that not only protects data but also enables business growth and innovation.
As we look toward 2027, the organizations that have successfully migrated away from the “castle and moat” mentality will be the ones best positioned to thrive in an increasingly digital and dangerous world.